Black Flag XMR Miner 2026 has appeared in security briefings and threat reports as a stealthy cryptocurrency miner marketed with a suite of evasion and resilience features. This article provides a neutral, defender-focused analysis of the miner’s advertised capabilities, associated risks to organizations, indicators of compromise (IOCs) to monitor, and practical mitigation and incident-response recommendations for IT and security teams.
What is Black Flag XMR Miner 2026?
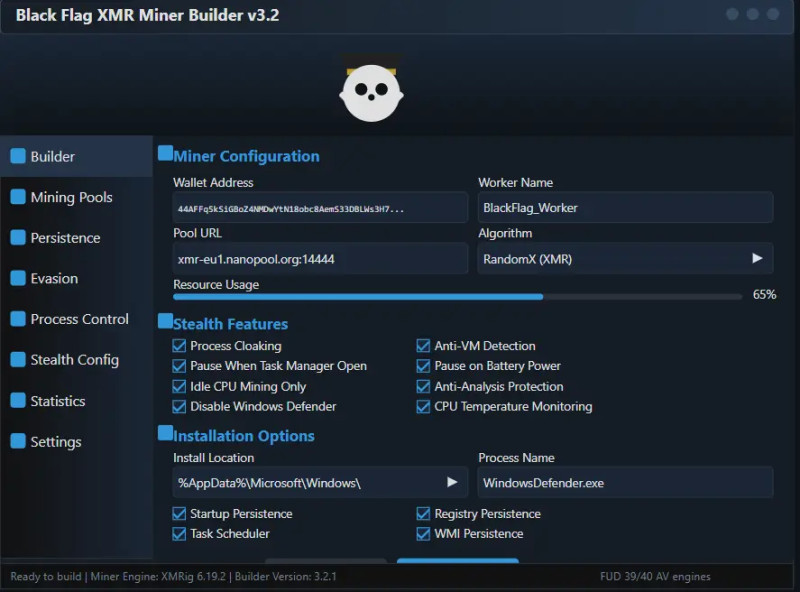
Black Flag XMR Miner 2026 is described in underground forums and security advisories as a professional-grade Monero (XMR) mining payload that prioritizes stealth and persistence. While researchers debate the origin and distribution vectors, defenders should treat any miner with these characteristics as cryptojacking malware and act accordingly to protect systems and network resources.
Advertised capabilities (high-level)
According to reports and sample descriptions shared with analysts, the miner is associated with — or claimed to include — the following capabilities (presented here purely for defensive awareness):
-
Silent XMR mining (aimed at low CPU visibility)
-
Compiled crypter to evade detection
-
SSL/TLS support for encrypted communications
-
Domain fallback support for command-and-control resilience
-
Watchdog that restarts the miner if it stops
-
Memory injection to avoid writing payloads to disk
-
“Process watch” to pause mining when specific user processes run
-
On-the-fly configuration updates
-
Integration with XMRig proxy setups